How To Collect Event Logs In Windows 7
Windows Consequence logs is one of the first tools an admin uses to clarify bug and to meet where does an issue come from. But it is not the merely way you tin use logged events. In this article, I will prove you lot how to employ PowerShell and Get-EventLog to perform some Consequence Log magic. But first, a few words almost the logs in general.

Event logging in Windows
First, there are 2 ways to access the events logged in Windows – through the Event Viewer and using the Get-EventLog / Get-WinEvent cmdlets. The Issue Viewer is an intuitive tool which lets yous find all the required info, provided yous know what to wait for. Searching the logs using the PowerShell has a certain advantage, though – yous can cheque events on the local or remote computers much quicker using the console. Information technology is an invaluable asset if you call up about server health monitoring. PowerShell lets you generate automatic reports about the most of import events to read while drinking your morn coffee.
Get-WinEvent vs Get-EventLog
You lot might wonder what is the difference betwixt Get-WinEvent and Go-EventLog. Get-WinEvent is a newer version of Get-EventLog. The cmdlets piece of work in a similar fashion, and Get-EventLog does the trick in most cases. According to a Microsoft documentation, the main difference is that Get-WinEvent works with "the Windows Event Log engineering science introduced in Windows Vista." To get a clearer explanation, you can utilise two uncomplicated cmdlets:
Go-EventLog -list
Go-WinEvent -ListLog * | where {$_.RecordCount -gt 0}
As you can see, Get-WinEvent is a clear winner when information technology comes to the amount of data it tin can access.
Heed that some attributes' names are dissimilar in those two cmdlets, so you might need to practice some translating if you lot desire to use the syntax of Become-WinEvent with the Get-EventLog cmdlet. If you want to know how to filter the results, simply piping the cmdlet to Get-Fellow member:
Go-EventLog application -newest 1 | Get-Member
Although Become-EventLog is a "legacy cmdlet," it however works like a amuse in most diagnostic cases. It also has 1 clear reward: you can use the -After and –Before attributes to filter results by date. Thanks to that, date-related queries are much quicker than pipe all results and trying to sift through them.
Earlier you get-go searching through the logs for specific events, it is a good idea to get to know the structure and get the full general idea of how the logging mechanism works. The Issue Viewer is the right tool to go y'all started on that.
The Issue Viewer
The amount of logging data can be overwhelming. It means that information filtering is your priority. In gild to get acquainted with the structure, you tin can either utilise the Event Viewer.
The quickest way to start the Event viewer is to use theWin+R key combination and executing eventvwr:
This action volition open the Event Viewer:
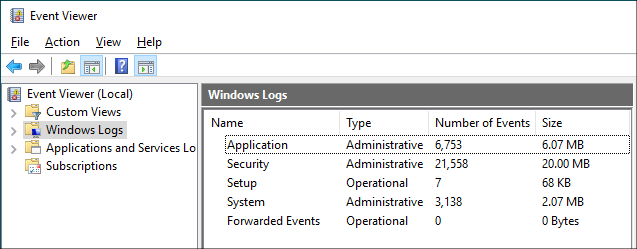
The tree on the left lets you browse through all Consequence Viewer's entries. The about used logs are Application, Arrangement, and Security.
Use PowerShell to diagnose problems on multiple computers
The biggest challenge of setting up the Go-EventLog or Get-WinEvent cmdlets is to filter results. Offset, you have to know what to await for, next – you lot have to make certain that your query does not crusade the PowerShell console to throw a fit. One way to run diagnostics is to apply the script below:
$servers = Get-TransportService;
foreach ($server in $servers)
{Write-Host "Scanning the event log of: " -NoNewLine; Write-Host $server;
Get-EventLog organisation -ComputerName $server -After (Get-Date).AddHours(-12) | where {($_.EntryType -Friction match "Error") -or ($_.EntryType -Lucifer "Warning")} | ft -wrap >> "C:/$server.csv";
Go-EventLog application -ComputerName $server -Afterwards (Get-Date).AddHours(-12) | where {($_.EntryType -Match "Error") -or ($_.EntryType -Match "Warning")} | ft -wrap >> "C:/$server.csv"}
The script pulls information about all Error and Warning kinds of events generated in the concluding 12 hours in System and Application logs for a list of servers. You can supervene upon the Get-TransportService cmdlet with another list of machines you desire to diagnose.
Checking login and logoff time with PowerShell
There are quite a few ways to check when a certain machine was turned on. If y'all simply need to check when was the showtime time a user logged in on a specific date, use the following cmdlet:
Get-EventLog organization -after (go-date).AddDays(-ane) | where {$_.InstanceId -eq 7001}
To learn when the figurer was turned on a specific date, you can select the get-go logged outcome:
$today = get-engagement -Hour 0 -Minute 0;
Go-EventLog system -subsequently $today | sort -Descending | select -First 1
Those cmdlets; however, volition not work if y'all want to monitor the usage of a shared computer.
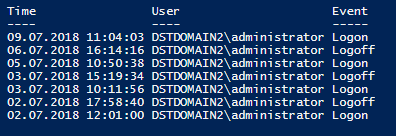
You could scan through the security events, looking for 4624 (logon) and 4625 (logoff) upshot IDs. However, the security log usually holds the greatest number of records and going through it tin exist extremely time-consuming. Fortunately, the system log also stores logon and logoff data and specifying the exact source of the log entry allows a relatively quick search. The script below returns a listing of logon and logoff events on the target figurer with their exact times and users for the last seven days.
$logs = get-eventlog system -ComputerName <name of the monitored computer> -source Microsoft-Windows-Winlogon -After (Get-Date).AddDays(-7);
$res = @(); ForEach ($log in $logs) {if($log.instanceid -eq 7001) {$blazon = "Logon"} Elseif ($log.instanceid -eq 7002){$type="Logoff"} Else {Go along} $res += New-Object PSObject -Holding @{Time = $log.TimeWritten; "Event" = $type; User = (New-Object System.Security.Principal.SecurityIdentifier $Log.ReplacementStrings[one]).Interpret([Arrangement.Security.Principal.NTAccount])}};
$res
Consequence:
If you demand more detailed results, you could add the Security log events IDs 4800 and 4801 for lock and unlock events. Mind that this will crave you to run another Get-EventLog script to get info from the Security log. It will also significantly increase the time your PowerShell console will demand to finish the job.
Further Reading:
- Managing users' Outlook rules from Substitution Management Shell (with PowerShell)
- Bulletin tracking logs in Commutation Server
Source: https://www.codetwo.com/admins-blog/how-to-check-event-logs-with-powershell-get-eventlog/
Posted by: mcginnismanday.blogspot.com

0 Response to "How To Collect Event Logs In Windows 7"
Post a Comment